I’ve had a few people ask me over the last couple of days why their vSphere Web Client SSL certificates are not being updated when they change the vCenter SSL Certificate as per my article The Trouble with CA SSL Certificates and vCenter 5. The normal reason for this is that the vSphere Web Client, when installed on the vCenter Server, stores it’s SSL certificates in a completely different location to that of vCenter Server. I’ve also since found out since publishing my other articles that this is true for the Inventory Service also. Why both of these services when installed on the vCenter Server don’t leverage the same SSL certificate location I’m not sure. My previous article has now been updated to include the replacement of the SSL cert for the Inventory Service, and also mentions the vSphere Web Client when installed on the same system as vCenter.
If you want a way to fully manage the certificate lifecycle and replace certs automatically then you’ll want to check out vCert Manager – Changing VMware SSL Certs Made Easy. This will completely automate the SSL certificate process in vSphere environments.
The default location for the vSphere Web Client certificates is C:\Program Files\VMware\Infrastructure\vSphere Web Client\DMServer\config\ssl. You will need to restart the vSphere Web Client, or reboot the vCenter Server to load the new certificates into memory. You will then be able to log into the vSphere Web Client to test that it is still functioning.
Updated: In most cases you should use the default keystore password of testpassword for your pfx file. If you chose to use a custom password for your keystore you will need to update the tomcat configuration files with the new password. Please refer to VMware KB 1013472 – vCenter Server Service Status plug-in cannot be enabled. However this doesn’t offer any additional security as the keystore password is still stored in clear text in these configuration files either way. Access to the filesystem locations of the important certificate and configuration files should be locked down to prevent any unauthorized access. Thanks to Dan Corrigan for raising this in the comments below.
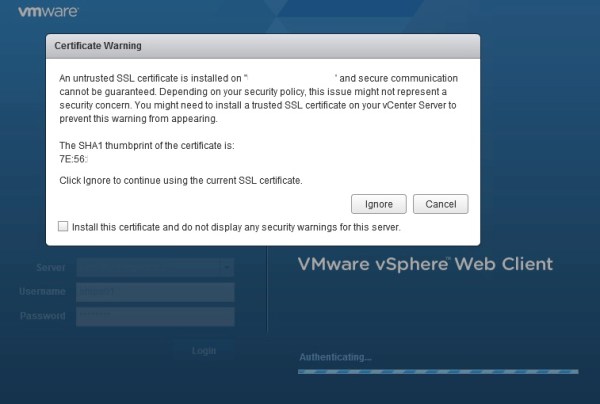
You may notice that when you change the vCenter SSL Certificate that vSphere Web Client will pop up a warning box the when you attempt to log in. The warning box will say that secure communication can’t be verified. This is due to the thumbprint of the vCenter Server SSL Certificate being different to what vSphere Web Client recognized when it was registered with vCenter. If you click install the certificate and ignore to continue it will not prompt you again on this system. You will need to unregister the vCenter system on the vSphere Web client using the admin-app url, and then re-register it again. To do this you will need to log into the vSphere Web Client system using RDP (Assumes Windows Version), then opening https://localhost:9443/admin-app in a web browser. Once the vCenter System is registered with the new thumbprint the warning dialog box should not be displayed again.
WARNING: Under normal circumstances you should not blindly ignore these types of warning messages and should not automatically just install certs and ignore to continue. You need to institutionalize Standard Operating Procedures that question every time a warning dialog such as this is present and you must verify the authenticity of the certificate. Here is an example of the warning box with the vCenter Server and SHA1 thumbprint obscured.
So you don’t have to jump back to my previous article just to find the default location for the Inventory Service SSL Certs it is C:\Program Files\VMware\Infrastructure\Inventory Service\ssl.
This post first appeared on the Long White Virtual Clouds blog at longwhiteclouds.com, by Michael Webster +. Copyright © 2012 – IT Solutions 2000 Ltd and Michael Webster +. All rights reserved. Not to be reproduced for commercial purposes without written permission.




Hey Michael,
thank you for great posts about certificates and their installation in vmware environment.
i have changed inventory and web client certificates and reregistered vcenter in admin-app but still have same certificate error as on your screenshot. Meanwhile certificate in the address bar is accepted by browser itself. re-registering doesn't help
any ideas?
thanks
Hi Behruz, I've had this before as well. The customer rebooted their system in one instance and the problem went away. Did you check that when vCenter was registered again the correct thumbprint was loaded? You should find after restarting the services, or rebooting the vSphere Web Client, that the error goes away. You may have to re-register again and double check the thumbprint is the correct one for the vCenter certificate.
I have tried to restart system re-register vcenter 10 times and it doesn't help when I posted my frist question to you regarding Web Client I have used esxi instruction to generate certificates for vCenter and Web Client, afterwards I have realized that I have missed another instruction from you for vCenter. Today I have prepared new certificates for vCenter, Update Manager (I'm using same certificate files for Web Client from vCenter) and I'm still have problem with Web Client. I have compared thumbprint and they are the same in warning windows from Web Client and certificate itself. My another problem is the VMware vSphere Profile-Driven Storage Service fails to start.
[…] vSphere Web Client SSL Cert not updated after vCenter SSL Cert Changed […]
Hiya Michael,
Thanks for this great tip to also place the SSL certs in the Web Client directory.
Thanks.
[…] to change the self-signed SSL certs in a few of the VMware components, such as vCenter Server 5, vSphere Web Client, and ESXi 5 Hosts. All without any discussion about why you would want to do it at all. So why do […]
If you have a password protected private key, you will have to edit the password used for your pfx in D:Program FilesVMwareInfrastructurevSphere Web ClientDMServerconfigtomcat-server.xml
You also have to update D:Program FilesVMwareInfrastructuretomcatconfserver.xml
Reference:
http://kb.vmware.com/kb/1013472
BTW, Great articles!
Thanks Dan. I have updated the article with reference through to the VMware KB. I have not used this in the past as I don't believe it offers any additional security as the password is still contained in clear text in the configuration files. But I do acknowledge some companies security policy makes this mandatory. In a vSphere environment there are multiple tomcat instances and configuration files that would need to be updated. Not all of them are obvious, not all of the passwords are documented, and changing them is not always supported. Great care needs to be taken if you are changing from default settings. Thanks very much for the comment it is greatly appreciated.